Protect Yourself Against New Forms Of Malware Such As Ransomware Or Fake Alerts
There’s been an increase in a new trend in malware and it is important to know how to protect yourself against such new forms of malware such as Ransomware or fake alerts. Conventional malware that manifests in the form of a plugin or an executable is no longer the preferred medium of infection. These days, the crooks are getting more creative with their malware since it is easy for free Anti-Virus to detect and block any form of executable. The only way to get around this block is to deliver the content through legit means, such as through a browser by setting shortcuts to point to the malicious site.
In this article, I will touch on some of the new forms of malware that are starting to take the world by storm and most likely you will get to know someone who has been hit by such new forms of malware.
1. Ramsomware
This is one of the most frightening forms of malware in the new century. It can be delivered commonly via email attachments that are named in a way that seems innocent looking to anyone, with names like invoice, flight tickets, delivery packages and even bills. If you click on those attachments, you are actually running an executable application that encrypts your files and folders, after which, your system’s wallpaper will be changed and you will be directed to pay to get your computer files unlocked. In fact, given sheer amount of variations of methods that Ransomware can be delivered to your system, some crooks go to the extent of inserting a link in a harmless pdf file to get you to click on. This is to prevent their email attachment from being blocked or stopped by spam filters. I have listed some of the ways that Ramsomware are delivered.
- Sent in the form of attachments without disguising the attachment. Generally be careful of files with random extensions. For example, vbs, hta, exe etc.
- Sent in the form of PDF or documents with a link in the file that will direct the user to a malicious website with in turn, infects the user
- Sent in the form of a seemingly harmless email with a link in the email itself asking you to verify if you ordered a package or a flight ticket or a puchase.
2. Modified Internet Explorer shortcuts
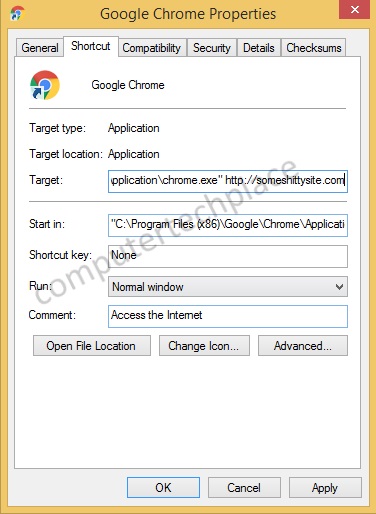
This is becoming increasingly common concept employed by malicious software. I suppose they stole the idea from legitimate Anti-Virus software that will block the URL with its own through the program shortcut path. By doing so, it is less likely for the user to be routed to another website should the malicious software change the default homepage in the browsers. It is undetectable by most malware scanners when they employ such a technique as there is not a trace of application or physical file in the system. Should you feel that you get into a situation where you are unable to remove the malware in your browser, check the shortcut by doing a right click of the Internet Explorer and check the properties. You may see a website at the end of the shortcut at the end.
3. Fake advertisers
You can be lured into clicking on an advertisement that sounds legitimate. For example an advertisement on the presidential elections. You click on it, but it routes you to a page that seems to have information on everything that you are interested in. However, for some reason, it expects you to share with 50 users for no reason at all, even before you start watching the video. Or asking you to like the video by force. Usually, such sites manifest themselves with false codes that make you agree to some instructions behind the background that will result in you changing certain settings in your PC. Thus, in any event, most sites that force a “like” or “share” pop up on you before you even watch or read anything are highly suspicious. I suggest you leave the site immediately.
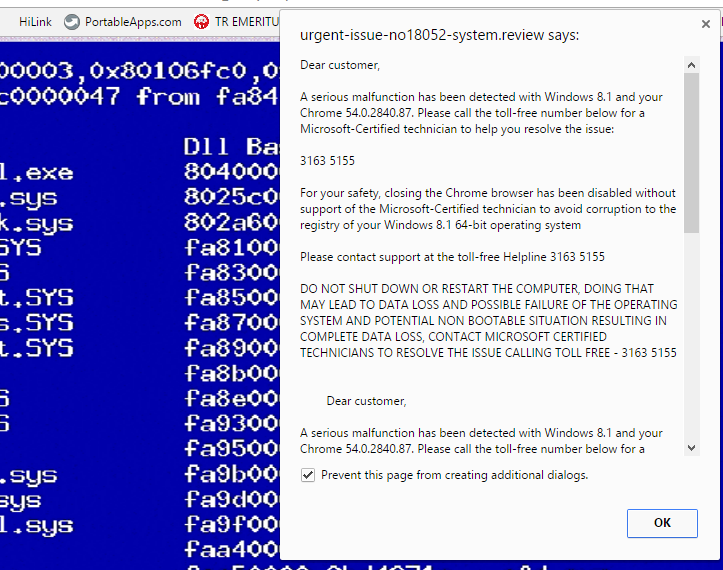
4. Advertisements in the form of Fake Errors
Getting infected in this manner is one of the most common of them all. More of the users who are not tech-savvy enough will not see through the disguise. The ads will leverage on fear mongering and scare the user in saying that their PC has hundreds of errors that require fixing, or claim that they can speed up the system. Most users will download, since most of these alerts are designed to look like they are from Microsoft. One way of the best example out there now is the Fake BSOD. It is so powerful that it does not allow you to close it. In fact, this advertisement did nothing to your PC, all it does is to have a message asking you to pay to stop it. But you cannot stop it, this is an ad that you can get hit by any website. What you can do, is be careful and stay claim, you can stop it, all you have to do it to try to close it twice and after which, there is a dialogue box in the middle that says, prevent this page from creating additional dialogs. Put a tick on that and after which you can close it like any other advertisement.

In summary, how to protect yourself?
The most reliable protection of all will be your own sense of situational -awareness and always be on guard. Have that sense of caution even though you are protected at home. Even though you are not physically out in the world, you are digitally connected and exposed to outside world. Would you be accepting freebies and giving out your contacts if you are being approached by someone out there that you do not know? If your answer is, you will not give out or easily say say yes to strangers, then do the same the internet.
Here are some ways to protect yourself
1. Use Virtual Machines or Sandbox solutions.
While this may seem like a complicated solution that is too difficult for the average person to adopt. You can try the easy way out and that is to have an extra computer or laptop lying around. This laptop will be a fresh installation with no critical files at all. Use this laptop to do simple web surfing or check out anything that you don’t feel safe. Once you feel that you are certain that this file or application is deemed safe to use. Email it across to yourself and download it via your own email account or file share. That way you will not get hit by malware should you want to download the same piece of software but access a wrong link by accident because you did not remember the exact link that you initially download the file from.
In this way, even if you get hit by any form of malware, you can simply format and start all over again without losing anything at all. The same concept applies for Smartphones, like Android. Use Android emulators like Bluestack to test out apps first before you install it onto your own Android phone.
2. Use Time Freeze
I stumbled on a piece of software called Time Freeze. This piece of software will allow you to freeze any changes that you might make to your PC, but be careful not to enable this by accident when you are working on your project. Because everything that you saved will not be saved once you restart your PC. So it will protect you from any unauthorized actions or settings that the malware attempts to make.
3. Get a really powerful Anti-Virus
While this may sound pretty obvious to all, buying a paid Anti-Virus can really be the best solution you can get to arm yourself to the teeth. Some of the most reputable brands like Bitdefender and Eset Nod are so updated with the latest trends in town that you will have nothing to fear about. The downside of using a super strong Anti-Virus is that you may be blocked from using software like Bittorrent or proxy software.
I hope that you will benefit from this article and if you have any tips to share, do share with the community in the comments section below.

Leave a comment